Argyle is committed to the highest standards of data security, meaning that we don’t cut corners when it comes to encrypted data. So, how exactly are we keeping our user and customer information safe?
Our Policies
We enforce strict rules and processes with regard to encryption, authentication, and database access. As stewards of our customers’ data, we’ve built a stringent and well-documented system for managing any and all sensitive information.
Our policies ensure that personal data remains safe from both targeted attacks and potential vulnerabilities related to user error. With Argyle’s military-grade encryption standards, customers can rest assured that their information is protected against bad actors. However, we also understand that users don’t always make the most security-minded decisions when it comes to their personal information. Say Sara shares her password with a friend. It’s possible that that friend (either unintentionally or otherwise) could compromise that password. However, when Sara enters the password into an encrypted data transfer agent like Argyle that has built-in insurance and compliance measures, then there is considerably less risk.
Read on to learn more about our data security policies, processes, and practices.
Encryption and Key Management
Our Encryption and Key Management Policy contains our encryption standards and key management processes. Data in transit is required to have TLS 1.2+ encryption at a minimum, while data at rest is required to be encrypted with AES 256 or stronger. Keys are managed by Google KMS, are completely random, never leave KMS, and are rotated every 90 days. All encryption/decryption happens by sending data to KMS and getting back the result, and each operation is individually authenticated.
Users’ employer credentials are always stored encrypted with AES256. Other data is not encrypted in-memory, but all disk volumes are encrypted by Google Cloud. A few Argyle employees have admin access to the database, but all manual access leaves traces in audit logs. Internally, we store PII and other data in Google Cloud SQL database that is only connected to our private VPC network and not public internet. All access to the database must happen via SSL connections.
Passwords
Client and client user passwords are stored as hashes derived from 100000 rounds of PBKDF2-SHA256. We have validation requirements for a minimum length of 8, no common passwords, and no numeric passwords to further ensure data security. For authenticating in Argyle Console and Argyle Link, we use JWT tokens with a lifetime of 30 days and HMAC with SHA-256 signing. All JWT token claims are always verified by checking our DB, so a relatively long token lifetime still allows us to revoke access if needed.
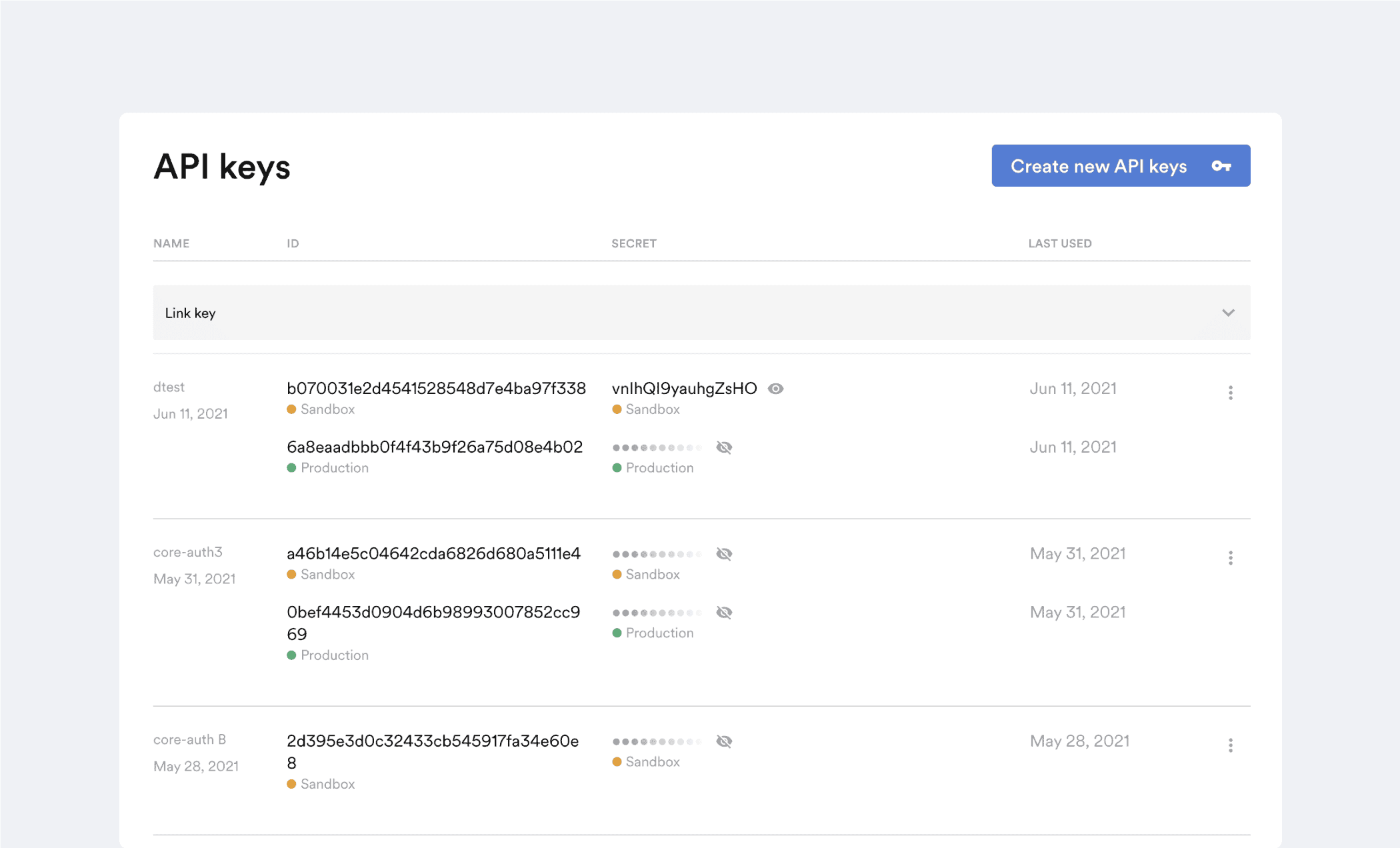
API Authentication
For API request authentication, we randomly generate API keys which are stored in our DB and are visible in Argyle Console. Clients can generate new keys and revoke old ones anytime via the Argyle Console. The Argyle API only allows client requests using strong Transport Layer Security (TLS) protocols and ciphers. Communication between Argyle infrastructure and data platforms is transmitted over secure encrypted tunnels. All requests to Argyle API must use HTTPS. We prevent the API from working over HTTP. Our websites, such as argyle.io, console.argyle.io, etc. also use HTTPS everywhere.
Messaging
Our services communicate to each other via RabbitMQ queues. To improve fault-tolerance, messages are persisted to disk while waiting to be processed. We never put unencrypted sensitive data into messages that are sent to those queues. In general, the sender usually encrypts the message with AES256 and the receiver has to decrypt it before doing any work. Keys are controlled using Google KMS and only Service Accounts of our GKE cluster nodes have rights to use those keys. Sensitive data like database SSL keys are stored using Bitnami’s kube-seal secret management service. It uses RSA with 4096 bit key to asymmetrically encrypt them with private keys accessible only from inside our GKE cluster.
Our data encryption protocols are national-security worthy
Powered by Google KMS, we keep all data securely encrypted at RSA 4096 (the same grade used by the U.S. military) with SHA-256 signing. Data sent to or from our infrastructure is encrypted in transit via industry encryption standards using Transport Layer Security (TLS). At rest, all data is subject to battle-proof encryption algorithms and stored using kubeseal secret management services. You can view our SSLLabs report here.
We’ve also made significant investments in data security certification and best practices for our users’ and customers’ peace of mind. Recently, Argyle became both SOC 2 Type 2 compliant and ISO 27001 certified. And our security team is as experienced and dedicated as they come.